TECHNOLOGY
How Modern Commercial Security Systems Reduce Business Risks
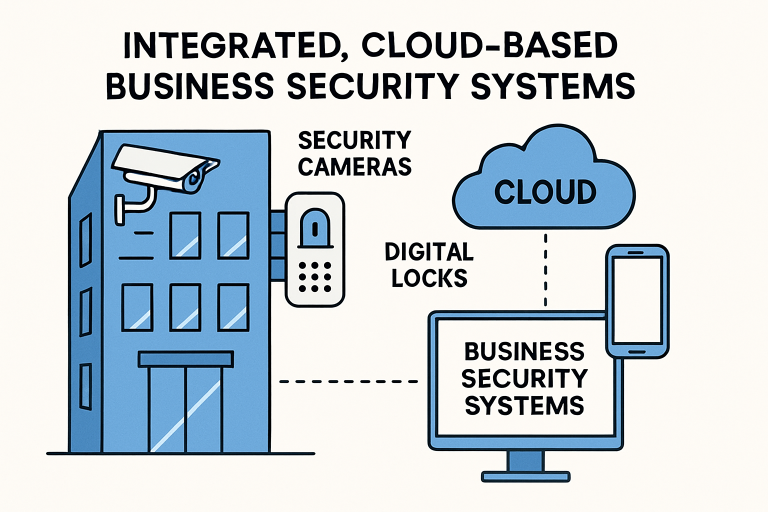
In an increasingly complex operating environment, businesses face a wide range of risks that extend beyond traditional concerns, such as theft or vandalism. Unauthorized access, internal misconduct, data breaches, and operational disruptions can all threaten continuity and financial stability. Modern commercial security systems have evolved to address these challenges through integrated technologies that emphasize prevention, early detection, and informed response. Rather than functioning as isolated tools, today’s systems combine physical security, digital monitoring, and automated controls to create a more resilient risk management framework.
Advancements such as intelligent surveillance, access control systems, and real-time alerts allow organizations to identify vulnerabilities and respond more effectively to potential threats. These technologies also support better decision-making by generating data that can reveal patterns, inefficiencies, or emerging risks. For businesses seeking to understand how these systems are designed and implemented in real-world settings, general industry resources like signalsolutions.com provide insight into the components and principles behind modern security infrastructure. Overall, commercial security systems play a crucial role in mitigating uncertainty, facilitating compliance, and enabling organizations to maintain safe and reliable operations without relying solely on reactive measures.
AI-Driven Video Surveillance
Surveillance technology has undergone a transformation with the integration of artificial intelligence. Gone are the days of relying solely on human monitoring and analog cameras. AI-driven video surveillance provides real-time analysis, enabling the rapid identification of suspicious activities or policy violations without human oversight. These intelligent systems can detect and classify objects, recognize faces, and alert security teams to anomalies, minimizing incident response times and often preventing crimes before they escalate. AI-powered surveillance is becoming a cornerstone for proactive business risk management.
Cloud-Based Monitoring and Remote Access
The adoption of cloud-based platforms has redefined how businesses monitor and control their security infrastructure. Cloud solutions allow for the centralized management of multiple locations, providing instantaneous access to live or recorded video feeds, access logs, and security events from any authorized device. This accessibility enables businesses to respond swiftly to emergencies, regardless of the location of their stakeholders.
Moreover, cloud-based systems can be scaled efficiently as a business grows, ensuring that new sites and users can be added with minimal disruption. Automated updates and cybersecurity features also provide protection against emerging digital threats, thereby reinforcing the overall security posture. This real-time, remote functionality proves invaluable for distributed teams and executives on the move.
 Advanced Access Control Systems
Advanced Access Control Systems
Modern access control extends far beyond traditional locks, utilizing technologies such as proximity cards, mobile credentials, and biometric authentication to enhance both security and convenience. These methods help prevent unauthorized entry and tailor access permissions to individual roles and schedules. For instance, cleaning staff may only have access to the building after hours, while IT personnel may have restricted access to server rooms.
Advanced access systems produce detailed audit logs, improving accountability and compliance—key considerations in regulated industries. Notably, smart access control can also integrate with other building systems, such as video surveillance and alarms, offering a unified response to threats and simplifying management for security personnel.
Integration of Physical and Cybersecurity
With the increasing convergence of digital and physical threats, integrating these security domains is vital. A physical breach often leads to cyber vulnerabilities, such as unauthorized access to servers or network devices. Accordingly, a unified approach that includes both on-premises and digital protections is essential for comprehensive risk mitigation.
Forward-thinking businesses develop strategies that monitor both access points and network events, closing potential gaps and strengthening incident response across the board. Industry authorities recommend implementing holistic policies and providing security training to all employees to ensure robust, integrated protection.
Mobile Access Control
Mobile devices are revolutionizing access control, eliminating the need for physical keys and cards. Employees and visitors receive unique digital credentials on their smartphones, which can be updated or revoked instantly if a device is lost or an individual’s role changes. This system significantly reduces the risks and administrative burdens associated with lost or duplicated keys.
Mobile access also enhances user experience, offering convenience and flexibility for businesses with remote work arrangements or multiple branches. With seamless integration into cloud-based monitoring, mobile control further streamlines facility management and emergency response protocols.
Data-Driven Security Planning
Gathering and analyzing security data is critical for identifying trends and making informed decisions about risk mitigation. By integrating data analytics and AI, security teams can predict incident hotspots, optimize resource allocation, and create actionable insights for ongoing protection. For example, analytics solutions can identify which entrances face the most traffic or which times are most prone to security incidents, enabling businesses to focus efforts where they’re needed most.
Data-driven strategies not only enhance prevention but also help justify investments by demonstrating measurable improvements in safety and efficiency. Companies that leverage analytics witness reductions in both security breaches and operational costs, supporting long-term business resilience.
Sustainable Security Solutions
Sustainability is becoming increasingly important in security deployments. Businesses are adopting solar, LED, and low-power technologies to minimize their environmental footprint and reduce costs. Battery-operated, wireless sensors and solar-powered cameras provide reliable performance with minimal energy consumption and no complex wiring, making them ideal for both new builds and retrofits.
By selecting eco-friendly security products and implementing green policies, businesses demonstrate commitment to environmental responsibility while simultaneously lowering utility expenses and maintenance needs. These choices align with broader corporate social responsibility initiatives and appeal to environmentally conscious stakeholders.
Conclusion
Modern commercial security systems are crucial for mitigating business risks and fostering a safe, resilient organizational culture. Embracing AI-driven surveillance, cloud-based management, advanced and mobile access control, and the convergence of physical and cyber protections provides companies with a layered, responsive defense against today’s threats. Combining data-driven planning with sustainable technologies further amplifies the benefits, enabling organizations to operate confidently and responsibly in a dynamic risk landscape. The businesses that keep pace with these security innovations will be best equipped to protect their people, property, and reputation well into the future.
TECHNOLOGY
Supporting OEM Efficiency with Application-Ready Power Solutions

In the world of Original Equipment Manufacturing (OEM), speed and precision are everything. The market demands devices that are smarter, faster, and more reliable, putting immense pressure on manufacturers to streamline their production lines without sacrificing quality. When every second counts, the components that go into the final product matter just as much as the assembly process itself.
One often-overlooked area where efficiency gains can be found is power connectivity. While it might seem like a minor detail in the grand scheme of complex machinery or consumer electronics, the choice of power solution can have a ripple effect throughout the entire manufacturing lifecycle. Shifting from generic off-the-shelf components to application-ready power solutions is proving to be a game-changer for OEMs looking to optimize their operations.
By integrating power solutions designed specifically for the application at hand, manufacturers can reduce assembly time, minimize compliance risks, and ultimately deliver a superior product to the market faster.
The Hidden Costs of Generic Components
For years, the standard approach for many OEMs was to procure generic power cords and connectors. The logic was simple: these parts are commodities, so why complicate the supply chain? However, this “one-size-fits-all” mentality often leads to hidden inefficiencies that accumulate over time.
Generic cords often come in standard lengths that don’t quite fit the specific chassis of a device, leading to cable management headaches. Excess cabling needs to be coiled, tied, or tucked away, adding manual labor steps to the assembly process. Conversely, cords that are slightly too short can cause strain on connections, leading to potential failure points and warranty claims down the road.
Furthermore, compliance is a major hurdle. Navigating the labyrinth of global safety standards—UL, CE, VDE, CCC—is a complex task. Relying on generic suppliers who may not fully understand the specific regulatory requirements of the end device’s destination market can lead to costly certification delays.
What Are Application-Ready Power Solutions?
Application-ready power solutions are the antithesis of the generic approach. These are power delivery systems—cords, plugs, connectors, and power distribution units—that are engineered or pre-configured to meet the exact specifications of the OEM’s product and production environment.
This goes beyond just length. It involves selecting the right jacket material for the environment (e.g., medical-grade materials for hospitals or ruggedized rubber for industrial sites), ensuring the correct plug angles to save space, and pre-certifying components for global markets.
When a power solution is “application-ready,” it arrives at the factory floor prepared for immediate integration. There is no need for modification, no struggle with excess slack, and no worry about whether the plug fits the socket in a specific export country.
Streamlining Assembly and Inventory
The primary benefit of this approach is the direct impact on manufacturing efficiency.
Reduced Assembly Time: When a power cord is cut to the precise length required and outfitted with the correct connector angle, the installation process becomes seamless. Workers spend less time managing cables and more time on high-value assembly tasks. In high-volume production, saving even thirty seconds per unit translates to massive time savings over a production run.
Simplified Inventory Management: Sourcing application-ready solutions often means working with a partner who handles the complexity of SKU management. Instead of stocking dozens of different generic cables and adapters to cover various scenarios, OEMs can stock specific, consolidated part numbers that are ready for the assembly line.
Enhanced Product Reliability: A connection that fits perfectly is a connection that lasts. Eliminating strain on ports and reducing the clutter inside a device improves airflow and reduces the risk of overheating.
The Role of Customization in Efficiency
While “custom” often implies “expensive” or “slow,” in the context of OEM power supply, it actually drives efficiency. This is where custom power cords play a pivotal role.
Consider a medical device manufacturer producing a mobile cart for hospitals. A standard black PVC cord might be functional, but it poses cleaning challenges and may not withstand harsh hospital-grade disinfectants. By utilizing custom power cords designed with specific jacket materials and hospital-grade plugs, the manufacturer ensures the product is durable and compliant right out of the box.
Additionally, customization allows for branding opportunities and user experience improvements, such as color-coding cords to help end-users identify connections quickly, reducing support calls and increasing customer satisfaction.
Navigating Global Compliance with Ease
Perhaps the most significant efficiency gain comes from regulatory compliance. Global OEMs face a patchwork of electrical standards. Selling a device in Japan requires different plug configurations and safety certifications than selling the same device in Germany or Brazil.
Partners providing application-ready solutions act as an extension of the OEM’s engineering team. They stay abreast of changing regulations (like RoHS and REACH) and ensure that the power components are pre-certified. This prevents the nightmare scenario of a product launch being stalled because a generic component failed a safety audit in a target market. By offloading this complexity to power specialists, OEM engineers can focus on their core competency: product innovation.
Powering the Future of Manufacturing
As devices become more interconnected and compact, the margin for error in manufacturing shrinks. Efficiency is no longer just about moving faster; it’s about removing friction from every step of the process.
Application-ready power solutions represent a strategic shift from viewing power components as simple commodities to viewing them as integral parts of the product design. By prioritizing precise fit, material suitability, and regulatory readiness, OEMs can unlock new levels of operational efficiency.
The transition to application-specific power delivery is an investment in the production line’s fluidity and the final product’s quality. For manufacturers aiming to stay ahead in a competitive landscape, ensuring that their power solutions are as advanced as the devices they energize is not just a smart choice—it is a necessary one.
TECHNOLOGY
What Is jeusol3? Explained for Modern Tech

Introduction
In the fast-paced world of technology, new innovations are constantly emerging. One such breakthrough making waves is jeusol3. But what exactly is jeusol 3? This cutting-edge tool promises to reshape how we interact with technology and streamline processes across various industries. As advancements unfold, understanding its purpose becomes crucial for both tech enthusiasts and professionals alike.
Curious about how this revolutionary system came to be? Or perhaps you’re eager to learn about its features and real-world applications? You’re in the right place! Join us as we delve into the fascinating realm of jeusol3, exploring its journey from conception to potential future impact on the tech industry. Whether you’re a seasoned expert or just starting your tech exploration, there’s something here for everyone who wants to stay ahead in this digital age.
The History and Evolution of jeusol3
jeusol3 originated in the early 2020s, emerging as a response to the growing need for more efficient data processing solutions. Initially developed by a group of tech enthusiasts, it aimed to streamline complex algorithms and optimize performance across various platforms.
As demand for faster technology grew, jeusol 3 evolved. Developers continuously refined its architecture, enhancing scalability and flexibility. This adaptability made it appealing not just to programmers but also to businesses looking to innovate.
With each update, new features were introduced that expanded its capabilities. The community around jeusol3 began contributing tools and frameworks, fostering an ecosystem rich with resources and support.
Today, jeusol3 stands out as a robust solution in modern tech landscapes. Its journey from inception showcases how collaborative efforts can lead to groundbreaking advancements in technology.
The Features and Benefits of Using jeusol3
jeusol3 offers a range of innovative features designed to enhance user experience. Its intuitive interface simplifies complex tasks, making it accessible for both seasoned professionals and newcomers alike.
One standout feature is its robust security protocol, ensuring data integrity and privacy. This aspect is vital in today’s tech landscape where cybersecurity threats are rampant.
Another significant benefit is its scalability. As businesses grow, It adapts seamlessly to changing needs without compromising performance or speed.
Additionally, the platform supports integration with various tools and systems. This flexibility allows users to streamline workflows effectively, improving overall productivity.
Users also appreciate its real-time analytics capabilities. With instant feedback on performance metrics, stakeholders can make informed decisions rapidly.
Jeusol3 empowers organizations by providing essential tools that drive efficiency and innovation across diverse sectors.
Real-world Applications of jeusol3 in Modern Technology
jeusol3 is making waves across various sectors in modern technology. One notable application is in the realm of artificial intelligence. By enhancing data processing capabilities, it allows for more efficient machine learning algorithms.
In healthcare, It facilitates better patient outcomes through advanced predictive analytics. Medical professionals can analyze vast amounts of data quickly to identify trends and potential health risks.
The gaming industry also benefits significantly from this innovative technology. Developers use jeusol3 to create immersive experiences that adapt in real-time based on player behavior.
Moreover, its impact extends into smart cities where it optimizes resource management and energy consumption. This leads to not only cost savings but also a reduced environmental footprint.
Finance too has seen improvements with jeusol3. It enables faster transaction speeds while maintaining high security levels, streamlining processes for banks and customers alike.
How to Get Started with jeusol3
Getting started with jeusol3 is straightforward. First, ensure your system meets the required specifications. You’ll need a compatible operating environment to maximize its potential.
Next, download the official jeusol 3 package from the website or repository. Installation typically involves running a simple command in your terminal or executing an installer wizard.
Once installed, take some time to explore its user-friendly interface. Familiarize yourself with the layout and available tools that will help you leverage its capabilities effectively.
Joining online forums or communities can also enhance your understanding of jeusol3. Engaging with other users often leads to valuable insights and tips for optimizing usage.
Don’t hesitate to dive into tutorials and documentation provided by developers. These resources are treasure troves of information that will aid you on your journey with jeusol3.
Comparison with Other Similar Technologies
When looking at jeusol3, it’s essential to compare it with similar technologies. One contender is blockchain, known for its decentralized nature and security features. While both aim to enhance data integrity, It focuses more on real-time processing capabilities.
Another competitor is artificial intelligence. AI excels in automation and cognitive tasks but often lacks the collaborative framework that jeusol3 provides. This makes jeusol3 an attractive option for teams seeking efficient communication across platforms.
Cloud computing also enters the mix. It offers flexibility and scalability but can sometimes fall short in terms of speed and immediate accessibility—areas where jeusol3 shines.
Each technology has its unique strengths, yet none deliver the comprehensive integration that jeusol3 promises. The interplay between these technologies will likely shape future innovations as they evolve together in a synergistic digital landscape.
Future Developments and Potential Impact of jeusol3 on the Tech Industry
As jeusol3 continues to evolve, it shows promise in transforming various sectors within the tech industry. Developers are actively enhancing its capabilities, focusing on improved efficiency and adaptability.
One potential development is deeper integration with artificial intelligence. This could lead to smarter systems that learn from user interactions, streamlining processes across different applications.
Moreover, as more businesses adopt jeusol3, we might see a shift in how data is processed and analyzed. Real-time analytics could become standard practice, enabling companies to make informed decisions swiftly.
The collaborative aspect of jeusol3 also stands out. With an open-source approach gaining traction, developers worldwide can contribute ideas and innovations. This community-driven model may accelerate advancements even further.
In industries like healthcare or finance where precision matters greatly, jeusol3’s impact could redefine operational standards—making them not just faster but significantly safer too.
Conclusion: Is jeusol3 the Next Big Thing
As we delve deeper into the world of technology, jeusol3 emerges as a potentially transformative force. Its unique features and benefits set it apart, offering innovative solutions across various applications.
The history of jeusol3 showcases its evolution into a powerful tool that meets the demands of modern tech enthusiasts and professionals alike. With real-world applications spanning diverse industries, from healthcare to finance, its impact is undeniable.
Getting started with jeusol3 is straightforward, making it accessible for both seasoned developers and newcomers eager to explore this cutting-edge technology. When compared to similar platforms, jeusol3 stands out due to its ease of use and potential for integration within existing systems.
Looking ahead, the future developments surrounding jeusol3 are exciting. As advancements continue to unfold, there’s no telling how deeply ingrained it may become in our technological landscape. The question remains: Is jeusol3 poised to become the next big thing? Only time will tell if this innovative solution captures widespread attention and reshapes our digital experiences in profound ways.
TECHNOLOGY
Realitykubgs Revealed: What Makes It So Addictive

In an era where digital platforms compete for every second of our attention, one name has surfaced with a reputation for creating an unusually compelling hold on its users: Realitykubgs. Unlike traditional social media or gaming platforms, Realitykubgs offers a blended experience that seems to tap into fundamental human psychology with extraordinary precision. But what exactly is it, and more importantly, what makes Realitykubgs so addictive? This deep-dive analysis moves beyond surface-level observations to explore the intricate web of behavioral design, neuroscientific triggers, and socio-technical engineering that fuels its compulsive use.
Understanding the Realitykubgs Phenomenon
At its core, Realitykubgs is an immersive, interactive ecosystem. It blurs the lines between curated social content, gamified progression, and personalized reality simulation. Users don’t just consume content; they navigate a layered environment where their actions yield immediate, variable, and often emotionally charged feedback. This isn’t accidental. It is the product of deliberate design choices aimed at maximizing user engagement, session length, and return frequency.
The addictive nature of Realitykubgs is not a singular feature but a symphony of interconnected elements. To understand it, we must examine the components separately and then observe how they work in concert to create a powerful feedback loop that can be difficult to break.
The Core Psychological Hooks of Realitykubgs
The platform leverages several well-documented psychological principles:
-
The Variable Reward Schedule: This is the most potent hook. Inspired by B.F. Skinner’s operant conditioning experiments, Realitykubgs designs its interactions so that rewards (likes, new content, level-ups, virtual items) are delivered unpredictably. You don’t know when the next compelling piece of content or achievement will appear. This uncertainty triggers a dopamine-driven response, making the user compulsively check and interact, much like a person pulling a slot machine lever.
-
The Fear of Missing Out (FOMO): The ecosystem is dynamic and event-driven. Limited-time events, exclusive content drops, and real-time social interactions create a pervasive anxiety that stepping away means missing something unique or valuable. This social pressure is a powerful motivator for constant connection.
-
The Endless Scroll & The Goal Gradient Effect: There is no natural “end” to the experience. Content streams infinitely, and progression systems often have escalating yet never fully attainable goals. The Goal Gradient Effect states that individuals accelerate their behavior as they approach a reward. Realitykubgs uses progress bars, “almost there” notifications, and tiered achievements to make users feel perpetually close to the next milestone, encouraging continued effort.
-
Social Validation & Identity Investment: Users build profiles, avatars, and reputations within the platform. The investment of time and ego creates a “sunk cost fallacy,” making it harder to leave. Positive social feedback (comments, shares, virtual applause) within this invested identity delivers potent hits of social validation, tying self-worth to platform engagement.
Deconstructing the Addictive Loop: A Step-by-Step Analysis
The user journey in Realitykubgs can be mapped to a cyclical, self-reinforcing loop. This loop is the engine of its addictiveness.
Stage 1: The Trigger (External & Internal)
Every session begins with a trigger. External triggers are notifications, messages, or alerts from the platform itself. Internal triggers are emotional states—such as boredom, loneliness, curiosity, or stress—that the user has learned Realitykubgs can alleviate. The platform’s design ensures it becomes the default solution for these internal states.
Stage 2: The Action (Frictionless Engagement)
The action is the simplest behavior done in anticipation of a reward: tapping the app icon, scrolling, or clicking. Realitykubgs minimizes friction to this action. The interface is intuitive, loading times are minimized, and the entry point is always a single tap away on the user’s device.
Stage 3: The Variable Reward
This is the critical phase. The user takes action but receives a reward that is:
-
Variable: The content or outcome is not the same every time.
-
Salient: It is personally relevant, often through sophisticated algorithms.
-
Emotionally Resonant: It sparks curiosity, amusement, pride, or a sense of belonging.
This phase directly stimulates dopamine pathways, reinforcing the connection between the trigger and the action.
Stage 4: The Investment
The final stage asks the user to put something into the platform. This isn’t just money (though in-app purchases are a factor). More importantly, it’s data, time, content, and social capital. This could be:
-
Customizing a profile.
-
Posting a piece of user-generated content.
-
Building a friend list or community.
-
Learning the intricacies of the platform’s rules.
These investments increase the likelihood of the user returning (to see the return on their investment), thus seeding future triggers. The loop then begins again, stronger each cycle.
A Comparative Table: Realitykubgs vs. Traditional Media
To illustrate its unique positioning, the following table contrasts the engagement model of Realitykubgs with traditional digital and analog media.
| Feature | Traditional Media (e.g., TV, Static Websites) | Social Media 2.0 (e.g., Classic Social Networks) | Realitykubgs |
|---|---|---|---|
| Interaction Model | Passive consumption | Active but discrete interaction (like, share, comment) | Immersive, continuous participation |
| Reward Schedule | Predictable (scheduled programming) | Semi-predictable | Highly variable and unpredictable |
| User Identity | Minimal or non-existent | Curated personal profile | Invested avatar/alter-ego with social stakes |
| Feedback Loop Speed | Slow (ratings, reviews) | Fast (likes, shares in minutes) | Instantaneous and constant |
| Exit Points | Clear (end of show, article) | Somewhat clear (end of feed) | Ambiguous, intentionally obscured |
The Role of Algorithmic Curation and Personalization
Beneath the surface, the true architect of the Realitykubgs experience is its algorithmic engine. This system employs advanced machine learning to perform what is known as hyper-personalization.
-
Content Optimization: Every click, hover, pause, and skip is data. The algorithm constructs a psychological profile so accurate that it can predict what content will engage you at different times of the day, depending on your emotional state inferred from your interaction patterns.
-
Social Graph Exploitation: It doesn’t just understand you; it understands your network. By prioritizing content from individuals you have shown a subtle affinity for (even beyond explicit “friends”), it creates a sense of intimate, yet algorithmically-managed, social reality.
-
Adaptive Difficulty: In gamified segments, the challenge level adjusts in real-time to keep you in a state of flow—the zone between boredom and frustration where time seems to disappear. This is a key state for prolonged engagement.
The Ethical Implications and User Well-being
Understanding why Realitykubgs is addictive naturally leads to questions of ethics and responsibility. The deliberate use of persuasive design to capitalize on psychological vulnerabilities raises significant concerns.
-
Impact on Attention Spans: The constant context-switching and rapid reward cycles can rewire neural pathways, making sustained focus on slower-paced tasks (like reading a book or complex problem-solving) more difficult.
-
Mental Health Correlations: While not solely causative, heavy use of such platforms has been correlated with increased anxiety, depression, and feelings of social isolation, despite the platform’s promise of connection. The discrepancy between curated reality and personal reality can be stark.
-
Data Privacy and Manipulation: The depth of data required to fuel this personalization is immense. The user becomes both the consumer and the product, with their behaviors and preferences being refined and, critics argue, manipulated for maximum engagement.
For authoritative information on the behavioral science behind technology design, readers can refer to resources from the American Psychological Association (APA) on digital media or research from institutions like the Stanford University Human-Computer Interaction Group (a .edu resource).
Strategies for Mindful Engagement
Awareness is the first step toward regaining control. If you find your engagement with Realitykubgs or similar platforms becoming compulsive, consider these strategies:
-
Audit Your Triggers: Use device settings to turn off all non-essential notifications. This breaks the cycle of external triggers.
-
Introduce Friction: Move the app icon off your home screen, log out after each session, or set a timer. Adding even a small delay between impulse and action can empower conscious choice.
-
Schedule Usage: Designate specific, limited times for engagement instead of intermittent checking throughout the day. This contains the experience and prevents it from fragmenting your attention.
-
Curate Your Feed Actively: Use any available tools to mute, unfollow, or indicate “not interested” to train the algorithm toward less emotionally charged content.
-
Invest in Reality: Counteract the platform’s pull by consciously investing in offline activities that provide genuine, non-variable rewards—hobbies, exercise, and face-to-face social interaction.
For guidelines on healthy digital habits, public health resources like those from the National Institute of Mental Health (NIMH) offer science-based advice (a .gov resource).
Conclusion: Navigating the New Reality
Realitykubgs represents a zenith in the convergence of behavioral psychology and software design. Its addictive nature is not a flaw but a feature—a direct result of its mission to capture and retain human attention in an overwhelmingly competitive digital landscape. By deconstructing its mechanics—the variable rewards, the endless loops, the hyper-personalized algorithms—we empower ourselves as users.
We transition from passive consumers to informed participants. The goal is not necessarily to abandon these platforms entirely, but to engage with them intentionally, understanding the powerful forces at play. In doing so, we reclaim our time, our attention, and ultimately, our cognitive sovereignty. The insights presented here aim to foster a more authoritative and critical discourse around the technologies that shape our daily lives and minds.
Disclaimer: This article is an analytical examination based on observed design patterns and publicly available psychological research. It is intended for informational purposes and does not constitute professional psychological or medical advice.
-

 TOPIC4 months ago
TOPIC4 months agov4holt: Revolutionizing Digital Accessibility
-

 TOPIC6 months ago
TOPIC6 months agoMolex 39850-0500: An In-Depth Overview of a Key Connector Component
-

 TOPIC4 months ago
TOPIC4 months agoMamuka Chinnavadu: An Exploration of Its Significance and Cultural Impact
-

 TOPIC4 months ago
TOPIC4 months agoGessolini: Minimalist Aesthetic Rooted in Texture
-

 blog4 months ago
blog4 months agoBlack Sea Body Oil: A New Standard in Natural Skincare
-

 TOPIC6 months ago
TOPIC6 months agoDorothy Miles: Deaf Poet Who Shaped Sign Language
-

 TOPIC6 months ago
TOPIC6 months agoManguonmienphi: Understanding the Concept and Its Impact
-

 TOPIC5 months ago
TOPIC5 months agoArnav Deepaware: A Rising Computer Scientist and Innovator
