Tech
5 Key Trends Shaping Modern IT Management
Modern IT management is evolving rapidly, driven by a new wave of technologies and operational strategies. Keeping pace with these changes is not just a competitive advantage but a necessity for any organization looking to thrive in a digital-first era. Forward-thinking companies like Design Data are already adapting to these seismic shifts, reimagining their IT infrastructures and practices. By understanding and acting on emerging trends, IT leaders can position their organizations for efficiency, resilience, and strategic growth.
From artificial intelligence to sustainability, today’s IT environment is characterized by complexity and unprecedented possibilities. The effective fusion of human ingenuity and intelligent automation now sets the stage for innovative approaches to cybersecurity, infrastructure planning, and collaborative work. As the pursuit of business agility and digital transformation accelerates, the importance of proactive IT management cannot be overstated.
AI Integration in IT Operations
The adoption of artificial intelligence marks one of the most significant shifts in IT operations today. AI-driven tools automate repetitive workflows, enabling IT departments to redirect resources toward innovation and higher-level problem-solving. Predictive analytics powered by machine learning identifies system vulnerabilities before they can cause disruptions, and intelligent monitoring solutions can boost uptime and overall reliability. According to ZDNet, businesses implementing AI in their IT operations often experience substantial improvements in both cost efficiency and service quality. Forward-minded organizations are investing in these advanced technologies to streamline incident response, optimize infrastructure, and unlock real-time, actionable insights from vast quantities of operational data.
Further, the role of AI extends beyond internal operations. Customer support and user experience have also been transformed through intelligent chatbots, self-healing systems, and dynamic user interfaces. This evolution fosters a culture of constant improvement where technology automatically adapts to changing business requirements. The efficiency gains and improved operational accuracy resulting from AI adoption provide a clear competitive edge.
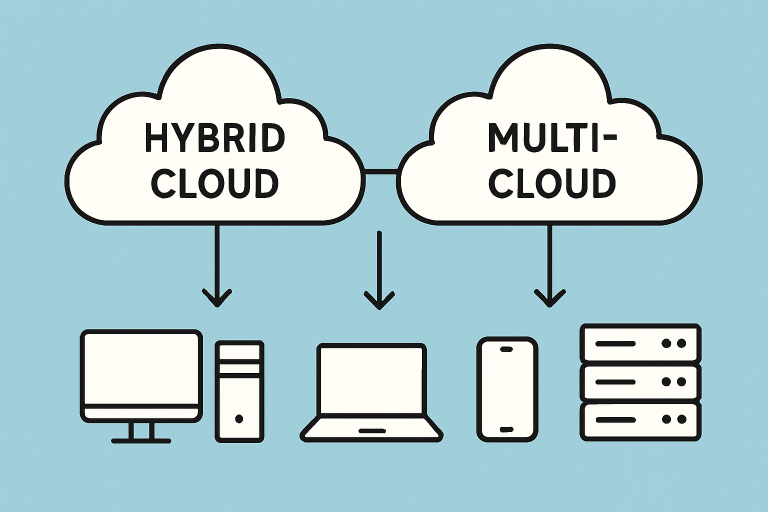
Adoption of Hybrid and Multi-Cloud Strategies
Cloud computing strategies have matured significantly in recent years. Rather than relying on a single provider or infrastructure, organizations now leverage a blend of private and public clouds for maximum flexibility and cost-effectiveness. A hybrid and multi-cloud approach allows businesses to choose the optimal environment for different workloads, while also reducing vendor dependency and providing additional layers of redundancy. This method is ideally suited to organizations with diverse application portfolios, regulatory requirements, or high-availability needs. Leading technology companies are increasingly touting the benefits of seamless cloud integration for operational agility and disaster recovery.
According to CIO.com, the move to hybrid and multi-cloud environments helps organizations manage costs, ensure business continuity, and deliver innovative services faster. These strategies give IT teams more granular control over data locality, compliance, and performance, thus enabling faster responses to fluctuating demands and regulatory shifts.
 Implementation of Zero-Trust Security Frameworks
Implementation of Zero-Trust Security Frameworks
The complexity and severity of cyber threats continue to escalate, rendering perimeter-based security models obsolete. Zero-trust security frameworks operate on the principle that organizations should not automatically trust any internal or external entity. Instead, continuous verification is required for every access request, regardless of the source. Identity and device authentication, least-privilege policies, and comprehensive monitoring form the backbone of this approach. As organizations adopt hybrid and multi-cloud models, zero-trust provides a robust foundation for safeguarding sensitive data and critical assets.
Zero-trust architectures are proving vital for defending against ransomware, insider threats, and phishing attacks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) strongly advocates the widespread adoption of zero-trust principles, highlighting their ability to reduce the attack surface drastically and swiftly contain breaches. As regulatory requirements grow ever more stringent, this approach enhances compliance and fosters a proactive security culture.
Supporting Remote and Hybrid Work Environments
Remote and hybrid work models are firmly embedded in the modern business landscape. IT leaders are under pressure to deliver seamless digital experiences for distributed teams while ensuring secure access to organizational resources without compromising productivity or agility. Robust collaboration platforms, virtual desktops, and advanced endpoint management tools are now prerequisites for success in this environment. Indeed, enabling a productive remote workforce extends beyond connectivity to encompass user experience, cyber hygiene, and change management.
To ensure business continuity and employee engagement, IT departments must deploy flexible solutions that support device diversity, network fluctuations, and asynchronous collaboration while maintaining robust security controls. As reported by Forbes, successful organizations are those that can deliver the right mix of tools, policies, and training that allows employees to excel from anywhere while safeguarding sensitive information.
Focus on Sustainability and Green IT
Sustainability is rising rapidly on the IT management agenda. With growing concerns over climate change and regulatory scrutiny, organizations are embracing green IT practices to reduce their environmental footprint and cut operational costs. Data center efficiency, virtualization, and cloud-native solutions are at the heart of this movement. The transition to paperless offices and the use of renewable energy for powering infrastructure are further examples of sustainable innovation in action.
Green IT initiatives not only respond to societal expectations but also deliver measurable benefits, including energy savings and improved brand reputation. As tech giants and startups alike join the push for carbon neutrality, sustainability is set to remain a key consideration in IT planning. According to The Verge, many of the world’s leading tech firms are already committing to clean energy and advanced recycling techniques to curb emissions across their global operations.
Modern IT management is fundamentally about anticipating change and aligning technology strategy with broader business goals. By embracing AI-driven automation, adopting versatile cloud strategies, bolstering security with zero-trust frameworks, supporting remote work, and prioritizing eco-friendly practices, organizations can not only overcome the challenges of the digital age but also turn them into lasting opportunities.
Tech
2rsb9053: Complete Overview and Key Specifications
Introduction
The world of industrial and mechanical components is vast, with bearings playing a crucial role in ensuring the smooth operation of countless machines. Among the numerous bearing codes and part numbers, the keyword 2rsb9053 stands out as an important identifier in the industry. Whether you’re a seasoned engineer, a procurement specialist, or just someone curious about how things work, understanding the 2rsb9053 can save time, effort, and money. In this article, I’ll break down everything you need to know about the 2rsb9053, including its specifications, uses, benefits, maintenance, and much more.
What is 2rsb9053?
The 2rsb9053 refers to a specific type of bearing—essential in reducing friction between moving parts and supporting radial and axial loads. The code 2rsb9053 encapsulates several features within it. Generally, such part numbers are determined by their manufacturer, and the coding system reveals vital details about the bearing’s dimensions, construction, seal type, and material.
Understanding the Naming Convention
- “2RS”: This typically denotes rubber seals on both sides of the bearing, which protect the internal components from contaminants like dust and moisture while retaining lubrication.
- “B9053”: This is the manufacturer’s designation for the series, bore size, or additional features.
Combined, the 2rsb9053 is a double-sealed bearing ideal for applications where keeping out dirt and holding in grease are top priorities.
Key Specifications of 2rsb9053
Let’s dive into the technical attributes that make the 2rsb9053 a sought-after component in various machinery.
Dimensional Details
While the exact size can vary depending on the specific manufacturer or application, here are the typical parameters:
- Inner Diameter: Often matches standard shaft sizes for compatibility
- Outer Diameter: Conforms to common housing bores
- Width: Sufficient to balance axial and radial loads
Always check the datasheet or technical drawing for the precise 2rsb9053 variant you’re sourcing, as dimensions can sometimes differ.
Material Construction
The 2rsb9053 is usually manufactured from high-quality chrome steel or stainless steel, sometimes featuring rubber components for seals. This ensures:
- Durability against wear
- Corrosion resistance, especially in humid or dirty environments
- Strength to handle significant loads
Sealing Mechanism
The “2RS” in 2rsb9053 signals double rubber seals on both sides:
- Purpose: Keep debris and moisture out
- Benefit: Long service life with minimal maintenance
- Drawback: Slightly increased rolling resistance due to seal friction
Lubrication
Bearings like the 2rsb9053 are often pre-lubricated:
- Type: High-performance grease compatible with metal and rubber
- Re-lubrication: Typically not required throughout their service life, thanks to the effective seals
Applications of the 2rsb9053
The versatility of the 2rsb9053 makes it a popular choice for a wide array of industries. Here’s where you’re most likely to encounter it:
Automotive Sector
- Wheel hubs
- Alternators and compressors
- Power steering systems
Industrial Machinery
- Conveyor rollers
- Electric motors and pumps
- Gearboxes and fans
Home Appliances
- Washing machines
- Vacuum cleaners
- Air conditioners
Agriculture and Construction Equipment
- Tractors
- Harvesters and mowers
- Earth-moving machinery
Benefits of Using 2rsb9053
The 2rsb9053 isn’t just a random bearing code; it’s trusted and selected for good reasons:
Extended Service Life
The double-sealed design inhibits contamination, greatly extending operational longevity.
Maintenance-Friendly
Pre-lubricated and effectively sealed—what’s not to like? It reduces downtime and the need for frequent checks.
Reliable Performance
Less friction, steady rotation, and proper alignment contribute to consistent output.
Environmental Protection
The robust seals mean the inner components are shielded from water, dust, and other invaders that could otherwise reduce the bearing’s life.
Installation and Maintenance Tips
If you’re working with a 2rsb9053, proper handling and installation matter. Here are my go-to tips:
Installation Best Practices
- Cleanliness is key: Make sure both shaft and housing are free of debris
- Alignment: Don’t force the bearing; press or tap it evenly
- Avoid direct impact: Use a bearing press or suitable tool
Maintenance Recommendations
Even though the bearing is sealed, periodic checks are wise:
- Monitor for noise or vibration: Early signs of wear
- Check temperature: Excessive heat hints at inadequate lubrication or misalignment
- Inspect seals: Damaged seals call for replacement, as contamination may follow
How to Identify Genuine 2rsb9053 Bearings
Counterfeiting is a real risk in the bearings market, and using subpar products can lead to machine breakdowns. Here’s what I do to verify:
- Check packaging: Should include correct branding, part number (2rsb9053), and manufacturer hologram or seal
- Request a datasheet: Authentic bearings come with detailed specs
- Buy from reputable sources: Trusted dealers or direct from manufacturers
- Inspect quality: Uniform finishing, no cracks or discoloration on seals
Frequently Asked Questions
Can I relubricate a 2rsb9053 bearing?
Usually, these bearings are maintenance-free due to their double-sealed design. However, if the seals can be carefully removed, re-lubrication may be possible.
Is the 2rsb9053 suitable for high-speed applications?
Yes, the robust design supports higher RPMs, provided installation and alignment are done correctly.
Are 2rsb9053 bearings interchangeable?
They often fit standard sizes, but always check the shaft and housing dimensions before swapping.
Conclusion
Choosing the right bearing can elevate your machinery’s performance and life span—the 2rsb9053 is a prime example of dependability and versatility. As with all technical components, ensure you’re sourcing authentic parts and following installation best practices. For those seeking a high-quality, low-maintenance bearing, the 2rsb9053 remains a top contender among professionals across industries.
Tech
What Is RealityKubgs? Full Explanation and User Guide

Introduction
When you first hear the term “RealityKubgs,” it sounds mysterious—almost like a hidden switch that unlocks a smarter digital world. In this guide, I’ll break it down in plain language: what RealityKubgs is (and is not), why it matters, and how you can use it effectively. I’ll also share practical steps, examples, and troubleshooting tips so you feel confident from day one.
What Is RealityKubgs?
RealityKubgs is best understood as a conceptual framework and toolkit that sits at the intersection of data orchestration, AI-driven automation, and immersive experience delivery. Think of it as a glue layer that connects your content, data pipelines, and intelligent decision-making so they can work together with minimal manual overhead.
At its core, RealityKubgs focuses on three pillars:
- Orchestration: Coordinating jobs, workflows, and services across heterogeneous environments (local, cloud, edge).
- Understanding: Applying machine learning and rule-based logic to interpret context from data in real time.
- Experience: Delivering outputs—dashboards, APIs, or immersive interfaces—that are responsive and personalized.
If you’re comfortable with ideas like “Kubernetes for workloads” or “streaming + inference,” you’ll feel right at home. If not, don’t worry—I’ll walk through it step by step.
Why RealityKubgs Matters
- Unified control plane: Rather than juggling tools for ETL, model serving, and content delivery, RealityKubgs offers a unifying abstraction.
- Speed to insight: It reduces the friction from data to decision, shortening cycles for analytics and AI-driven experiences.
- Reliability: It emphasizes observability and resilience, helping you avoid brittle, one-off integrations.
- Scalability: Designed to span laptops to clusters to edge devices without rewriting everything.
This makes it appealing for product teams, data engineers, and creators who want dependable automation without sacrificing flexibility.
Core Concepts
1) Resources
Resources are the building blocks—datasets, models, connectors, functions, and UI blocks. Each resource has a schema and lifecycle, and can be versioned for reproducibility.
2) Pipelines
Pipelines define how resources move and transform through stages (ingest → validate → enrich → infer → serve). They can be scheduled, triggered by events, or run on demand.
3) Policies
Policies are guardrails. They enforce data quality, governance, access control, and cost limits.
4) Runtimes
Runtimes are where things execute: CPU, GPU, or specialized accelerators. RealityKubgs dynamically maps workloads to the right runtime based on constraints.
5) Experiences
Experiences are the outputs users actually see—web apps, APIs, embeddings, or XR views. They’re declaratively defined so they can be deployed consistently.
Typical Use Cases
- Intelligent dashboards: Real-time metrics with automated insights and alerts.
- Model-serving APIs: Versioned models with traffic-splitting and canary rollout.
- Content personalization: Dynamic experiences that adapt to user behavior and context.
- IoT and edge analytics: Sensor ingestion, on-device inference, and centralized observability.
- Data app prototyping: Fast iteration from idea to production without re-architecture.
Architecture Overview
Control Plane vs. Data Plane
- Control plane: Manages configuration, policies, orchestration, and metadata. Think schedules, lineage, and access rules.
- Data plane: Executes workloads. Handles data movement, transformation, inference, and serving.
Components
- Registry: Catalog for resources with versioning and metadata.
- Scheduler: Coordinates jobs, honors SLAs, and supports event-driven triggers.
- Runner: Executes tasks within containerized sandboxes.
- Broker: Streams events and messages between components (e.g., Kafka, NATS).
- Observer: Collects logs, traces, and metrics for diagnostics and scaling.
Getting Started
Prerequisites
- Basic familiarity with containers and YAML (helpful but not mandatory)
- Access to a cloud account or a local machine with Docker installed
- Optional: GPU access for model inference
Installation Options
- Local Quickstart: Use a prebuilt container image that bundles the control plane and a minimal data plane.
- Cloud Deploy: Provision via Terraform templates, then bootstrap the control plane.
- Hybrid Edge: Install lightweight agents on edge devices and join them to the control plane.
First-Time Setup Checklist
- Create a workspace and configure authentication.
- Register your first dataset and model as resources.
- Define a simple pipeline (ingest → validate → infer).
- Set basic policies (data retention, access roles, cost caps).
- Deploy a sample experience (dashboard or API).
Hands-On: A Guided Example
Let’s build a simple anomaly detection dashboard for web traffic.
Step 1: Register Resources
- Dataset: traffic_events.json (schema: timestamp, user_id, url, latency)
- Model: anomaly_detector:v1 (isolation forest)
- Connector: http_sink for dashboard updates
Step 2: Define the Pipeline
- Ingest events from a stream
- Validate schema and filter malformed records
- Compute features (rolling mean, z-score)
- Run inference with anomaly_detector:v1
- Emit anomalies to the dashboard via http_sink
Step 3: Apply Policies
- Retain raw events for 7 days, features for 30 days
- Restrict PII access to admin role
- Cap daily compute to avoid runaway costs
Step 4: Deploy an Experience
- A single-page dashboard with a timeline and alert list
- Supports drill-down for user sessions
- Exposes an API endpoint for external tools
Step 5: Observe and Iterate
- Track model precision/recall and retrain if drift detected
- Use canary rollout for v2 model
- Set alerts for pipeline lag or error spikes
Best Practices
Design
- Start with a crisp problem statement and measurable outcomes.
- Keep resources small and composable for reuse.
- Prefer declarative specs over imperative scripts.
Operations
- Tag every resource with owner, purpose, and SLA.
- Version everything—datasets, models, and pipelines.
- Automate tests for data quality and pipeline correctness.
Security and Governance
- Adopt least-privilege roles and rotate keys.
- Encrypt data at rest and in transit.
- Maintain lineage and audit logs for compliance.
Performance
- Co-locate compute and data when possible.
- Use caching for hot paths and vector indexes for embeddings.
- Right-size runtimes based on actual workload profiles.
Troubleshooting Guide
- Pipelines stall or run slowly: Check scheduler backlog and resource quotas.
- Model inference errors: Verify model version compatibility with runtime image.
- Data quality issues: Revisit validation rules and add schema evolution strategies.
- Experience not updating: Inspect event broker and sink configuration.
- Unexpected cost spikes: Review policy caps and compute profiles.
FAQ’s
Is RealityKubgs open-source or commercial?
It can be implemented with open-source components or as a managed service; the philosophy is tooling-agnostic.
Do I need Kubernetes?
No, though container orchestration improves portability. RealityKubgs can run on serverless, VMs, or edge devices.
Can it handle streaming and batch?
Yes. Pipelines support both modes and can share resources.
How does it differ from traditional ETL?
It’s event-native, model-aware, and experience-oriented—beyond just moving data.
Roadmap Ideas
- Native feature store integration
- Built-in vector DB connectors
- Policy simulation for “what-if” governance
- No-code pipeline builder and templated experiences
Conclusion
RealityKubgs brings order and adaptability to the chaos of modern data and AI workflows. By unifying orchestration, understanding, and experience, it shortens the path from raw data to meaningful outcomes. Whether you’re prototyping a data app, serving models at scale, or shipping personalized experiences, the framework helps you move faster with confidence. Start small, observe everything, and iterate—your future self will thank you.
Tech
10.235.10205: Meaning, Technical Relevance, and Real-World Applications

In today’s fast-moving digital world, numbers and codes play an essential role in how systems identify, communicate, and manage data. One such number that often sparks curiosity is 10.235.10205. Though it may look like a random sequence at first, this combination of digits can represent much more depending on the context—ranging from a software version to a network identifier or even a dataset reference.
This article takes a deep dive into what 10.235.10205 could represent, how it’s typically used in modern technology, and why understanding such identifiers is important for professionals working with data, software, or IT infrastructure.
What Is 10.235.10205?
The term 10.235.10205 can be interpreted in several ways depending on its environment. It might represent a network address, a software version, a database identifier, or even a configuration number in a technical system.
When you see a number like 10.235.10205, you are likely dealing with a format that serves a specific function inside a computer or communication system. For example, in a networking environment, it may reference a local IP address from the private 10.x.x.x range. In a software context, it could be a version number, indicating a specific release or update of a program.
Understanding these numeric identifiers helps professionals trace problems, track updates, and organize digital assets more efficiently.
The Technical Background of 10.235.10205
Let’s consider some possible technical meanings behind 10.235.10205:
- Network Address Representation:
In IP networking, addresses that start with “10” are typically used for internal or private networks. If we interpret 10.235.10205 as a variation of an IP address (like 10.235.10.205), it could point to a specific device or subnet within a private network. Such addresses are commonly used in corporate LANs, VPNs, or cloud systems for secure communication. - Software Version or Build Identifier:
Many software developers follow versioning conventions such asmajor.minor.build. In this case, 10.235.10205 might represent a particular software release—perhaps version 10, minor update 235, build 10205. This allows developers to track changes precisely and helps users identify the version they are running. - Database or Record ID:
In large databases, numeric identifiers like 10.235.10205 are often used to label specific records, ensuring each entry is unique. This type of identification is essential for managing massive datasets efficiently. - System Configuration Number:
Some organizations assign configuration or reference numbers similar to 10.235.10205 to categorize machines, user accounts, or internal settings. This helps keep large systems consistent and traceable.
Why 10.235.10205 Matters in Technology
The importance of 10.235.10205 lies in how such identifiers simplify complexity. In a digital ecosystem that contains millions of components—servers, software builds, records, and devices—unique numeric values help maintain structure and order.
1. Simplifying Identification
Without identifiers like 10.235.10205, it would be nearly impossible to keep track of which version of a program or which server is being referenced. By using standardized numeric values, system administrators can instantly recognize and locate specific resources.
2. Enhancing Security and Organization
Identifiers such as 10.235.10205 can be used in secure network environments to mask the internal structure of systems. Private IP ranges like those beginning with “10” are not visible from the public internet, offering an additional layer of security and control.
3. Supporting Version Control
In software development, having a precise version number like 10.235.10205 ensures traceability. If a bug is found in a specific version, engineers can roll back, compare, or patch that exact build without confusion.
4. Improving Data Traceability
When used in databases, 10.235.10205 could represent a transaction, user, or device log entry. This helps maintain audit trails, which are crucial for security compliance and performance analysis.
Common Places Where You Might Encounter 10.235.10205
While 10.235.10205 might seem obscure, similar patterns appear in many areas of modern computing. Here are a few examples of where you might come across such a number:
Networking Systems
In internal networks or corporate infrastructures, numbers similar to 10.235.10205 often appear as identifiers for routers, printers, or internal services. These addresses ensure that each device has a distinct place in the communication framework.
Software Updates
If you’ve ever seen a program update listed as version 10.235.10205, it’s likely a specific build identifier that the development team uses to distinguish one release from another. Each digit communicates information about the software’s progress—major improvements, minor changes, or patches.
Data Analysis Platforms
In large analytical systems, every dataset or event might carry a reference number for indexing. A value like 10.235.10205 could identify a particular experiment, dataset, or log entry.
Cloud Infrastructure
In cloud computing, similar numbers are used in internal resource tagging or configuration management. This ensures that services remain organized even when scaling across hundreds of servers and regions.
The Importance of Context When Interpreting 10.235.10205
One critical point to remember is that context defines meaning. The same sequence—10.235.10205—could mean entirely different things in two separate systems.
- In a networking environment, it might represent an internal IP.
- In a software changelog, it could mark a new version release.
- In a data system, it might simply be a unique identifier.
Therefore, understanding where you encountered 10.235.10205 is essential before drawing any conclusions about what it signifies.
How to Work With Identifiers Like 10.235.10205
If you frequently deal with identifiers or codes like 10.235.10205, here are some best practices:
- Document Everything: Keep records of what each identifier represents. This ensures future team members can easily understand it.
- Maintain Consistent Formats: Whether it’s a version number or a network address, consistency in formatting prevents errors.
- Use Meaningful Structuring: Try to build identifiers that carry logical information—such as project codes, version stages, or locations.
- Protect Sensitive Identifiers: In secure systems, ensure internal identifiers (like those in the 10.range) aren’t exposed publicly.
The Broader Role of Numbers Like 10.235.10205 in Digital Systems
Numbers like 10.235.10205 represent the invisible structure behind the digital world. Every app, database, and network relies on unique identifiers to keep everything running smoothly. They are the DNA of information technology—allowing billions of components to coexist without confusion.
In an era of cloud computing, AI integration, and massive data exchange, structured identifiers are more vital than ever. They enable automation, enhance communication between systems, and help ensure reliability across complex infrastructures.
Even if 10.235.10205 is just one example, it stands as a reminder of how small details—numbers, codes, or labels—form the foundation of modern computing.
Final Thoughts on 10.235.10205
At first, 10.235.10205 may appear meaningless, but when examined closely, it symbolizes the precision and order that define digital technology. Whether it’s used for identifying software builds, mapping internal networks, or managing databases, such numeric structures are the unsung heroes behind efficiency and connectivity.
Understanding how to interpret and manage identifiers like 10.235.10205 can help IT professionals, developers, and data analysts navigate the digital landscape with greater confidence.
-

 TOPIC4 months ago
TOPIC4 months agov4holt: Revolutionizing Digital Accessibility
-

 TOPIC7 months ago
TOPIC7 months agoMolex 39850-0500: An In-Depth Overview of a Key Connector Component
-

 TOPIC4 months ago
TOPIC4 months agoMamuka Chinnavadu: An Exploration of Its Significance and Cultural Impact
-

 TOPIC5 months ago
TOPIC5 months agoGessolini: Minimalist Aesthetic Rooted in Texture
-

 blog5 months ago
blog5 months agoBlack Sea Body Oil: A New Standard in Natural Skincare
-

 TOPIC7 months ago
TOPIC7 months agoManguonmienphi: Understanding the Concept and Its Impact
-

 TOPIC7 months ago
TOPIC7 months agoDorothy Miles: Deaf Poet Who Shaped Sign Language
-

 TOPIC6 months ago
TOPIC6 months agoArnav Deepaware: A Rising Computer Scientist and Innovator
